Cloud-based accounting has become the backbone of modern finance departments, especially for businesses operating with distributed teams. Whether a company is fully remote or uses a hybrid model, cloud tools offer unmatched flexibility and real-time visibility. However, with this convenience comes the responsibility to secure financial data against cyber threats, human error, and non-compliance.
For small and mid-sized CPA firms, the stakes are even higher. A data breach or system compromise can lead to reputational damage, legal penalties, and lost clients. Ensuring the safety of cloud accounting systems is no longer a technical concern alone. It is a core business requirement.
This article lays out a complete framework of security best practices to help remote teams use cloud accounting tools without exposing their firms or clients to unnecessary risks. These practices apply whether you are using QuickBooks Online, Xero, Sage, FreshBooks, or any cloud-based solution.
Traditional in-office setups typically benefit from enterprise-grade firewalls, centralized IT support, and physical security layers. Remote teams, on the other hand, work from home networks, shared devices, and public Wi-Fi, all of which introduce greater security vulnerabilities.
Cloud accounting platforms contain highly sensitive data including tax ID numbers, payroll records, vendor bank information, and financial statements. If that information is compromised or altered, the financial and legal implications can be severe.
Common security threats include:
A proactive security strategy ensures that the convenience of remote work does not come at the cost of client trust and data integrity.
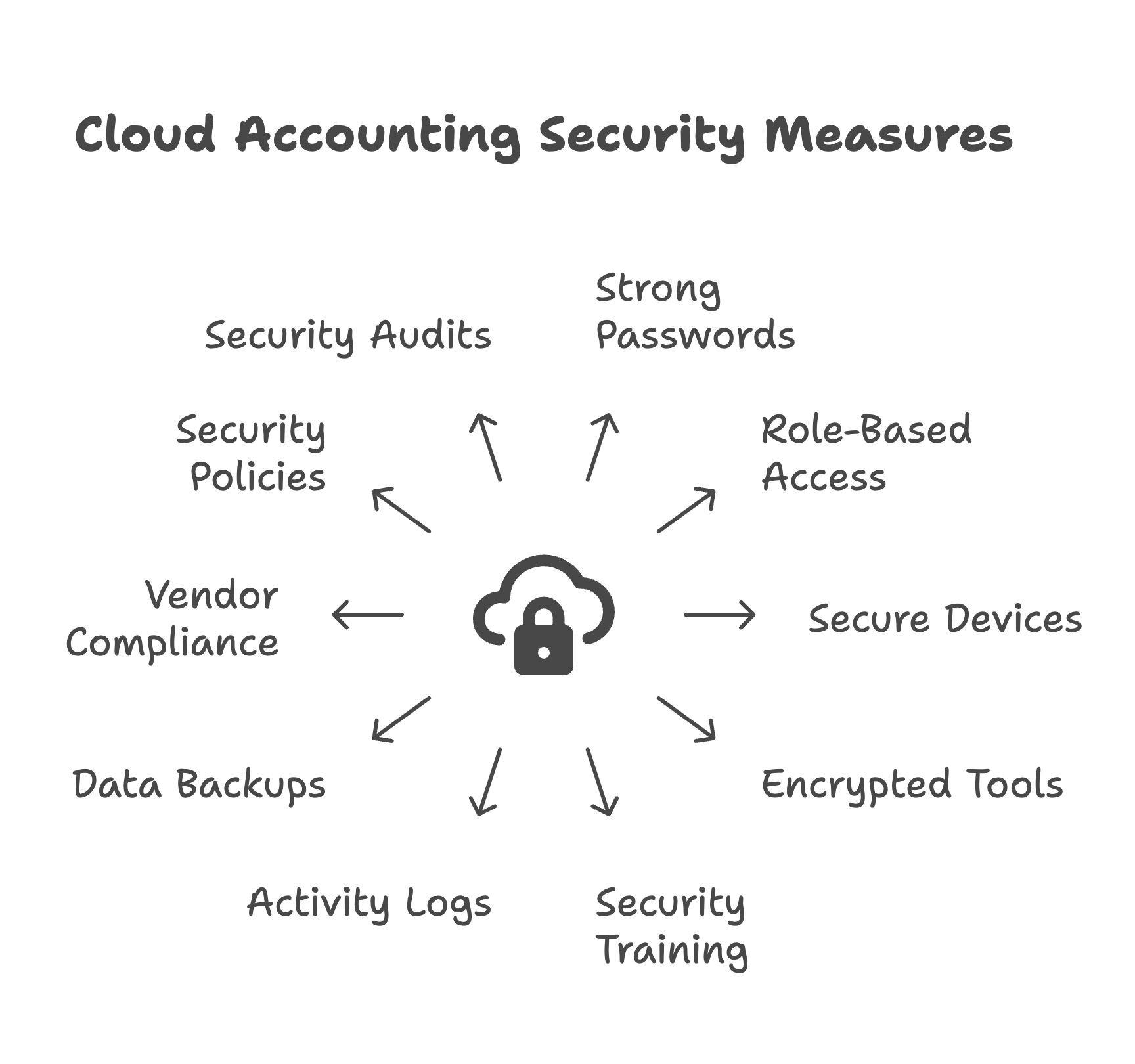
The first and most basic line of defense is proper credential management.
2FA adds an extra step to the login process by requiring a time-based code or a biometric confirmation. Even if a password is compromised, unauthorized access is blocked without this second factor.
Not every team member needs access to every part of the accounting system. One of the most common mistakes in cloud security is giving users more access than necessary.
This principle of least privilege ensures that employees can perform their duties without accessing unnecessary or sensitive data.
Remote employees often work on personal laptops or shared networks, both of which may lack enterprise-grade protection.
Firms should consider issuing company-managed devices preconfigured with the required security software and policies.
Financial documents are often shared for approvals, reviews, and audits. Email, unless encrypted, is not a secure way to transmit sensitive financial information.
Encryption prevents data leaks and ensures that even if a file is intercepted, its contents remain unreadable.
The best security system can fail if the users are not aware of how to use it properly. Human error remains the leading cause of data breaches.
Make security training a recurring event, not a one-time onboarding task. Offer updates whenever new threats or procedures emerge.
Most cloud accounting platforms offer detailed user logs that track login times, IP addresses, and actions taken within the system. These logs help you spot unusual behavior early.
Monitoring and logs are key to early breach detection and incident response.
Even with strong cloud systems, you should not rely on a single provider to protect your financial data completely. Data can be lost due to user error, outages, or platform failure.
Data loss can paralyze a business. Backups ensure continuity even if your primary cloud system fails.
Even if your firm uses best-in-class internal practices, the security of your financial data is also dependent on the third-party providers you work with.
Vetting vendors is essential to prevent weak links in your security chain.
Formal documentation not only helps your internal team understand expectations but also satisfies audit and compliance requirements.
Make sure these documents are easily accessible and reviewed at least annually.
Security is not a one-time task. Technology evolves, threats change, and new team members join. A regular audit ensures you are not falling behind.
Depending on your risk level and firm size, these audits may be monthly, quarterly, or biannually.
Cloud accounting software gives remote teams the power to collaborate in real time, automate bookkeeping tasks, and make smarter financial decisions. But it also creates new risks that must be managed carefully.
Strong passwords, access controls, encryption, training, and regular monitoring are the foundation of cloud accounting security. These best practices allow remote teams to operate securely without sacrificing speed or convenience.
For CPA firms supporting clients remotely or with offshore teams like Madras Accountancy, implementing and maintaining these controls is essential. It safeguards client data, protects the firm’s reputation, and builds trust in the systems that drive modern accounting.
If your firm is looking to scale its operations while maintaining rigorous security standards, we can help. Madras Accountancy offers fully compliant, secure offshore accounting support to U.S. CPA firms, with strict protocols aligned to best practices in cloud accounting security
Question: What are the essential security measures for protecting cloud accounting data with remote teams?
Answer: Essential cloud accounting security measures for remote teams include multi-factor authentication for all users, strong password policies with regular updates, encrypted data transmission and storage, and role-based access controls limiting user permissions to necessary functions. Implement VPN connections for sensitive data access, regular security training for team members, and automatic software updates for accounting systems. Use secure cloud platforms with SOC 2 compliance, maintain current antivirus software on all devices, and establish clear protocols for device security and data handling. Regular security audits, backup procedures, and incident response plans complete comprehensive security frameworks protecting sensitive financial information in remote work environments.
Question: How should businesses implement access controls and user permissions for remote accounting teams?
Answer: Implement access controls for remote accounting teams through role-based permissions granting minimum necessary access levels, regular user access reviews and updates, and automated user deprovisioning for terminated employees. Establish approval processes for access level changes, maintain detailed logs of user activities, and implement session timeouts for inactive users. Use principle of least privilege, granting users only access required for specific job functions, and implement segregation of duties even in remote environments. Regular access audits ensure permissions remain appropriate as roles change, while monitoring unusual access patterns helps detect potential security breaches. Document all access control procedures and maintain audit trails for compliance purposes.
Question: What VPN and network security requirements apply to remote accounting operations?
Answer: VPN and network security requirements for remote accounting include secure VPN connections for all accounting system access, encrypted communication protocols, and firewall protection on all devices. Use business-grade VPN services with strong encryption standards, avoid public Wi-Fi for sensitive financial work, and implement network monitoring for unusual activities. Require updated antivirus software, automatic security patches, and secure home network configurations for remote workers. Establish guidelines for personal versus business device usage, implement mobile device management for company devices, and provide secure equipment when necessary. Regular network security assessments and employee training help maintain protection standards across distributed teams.
Question: How can businesses ensure data backup and disaster recovery for cloud accounting systems?
Answer: Ensure data backup and disaster recovery through automated daily backups stored in multiple locations, regular backup testing and restoration procedures, and documented disaster recovery plans with defined recovery time objectives. Use cloud accounting providers with redundant data centers and guaranteed uptime levels, maintain offline backup copies for critical data, and implement version control for important documents. Test disaster recovery procedures regularly, train team members on emergency protocols, and maintain updated contact information for all stakeholders. Consider cyber insurance coverage for data breaches and system failures. Document all backup and recovery procedures, assign specific responsibilities, and ensure backup systems remain current with production environments.
Question: What employee training and awareness programs should businesses implement for cloud accounting security?Answer: Implement comprehensive security training programs covering password security, phishing identification, secure data handling procedures, and incident reporting protocols. Provide regular training updates on new threats, company security policies, and best practices for remote work environments. Include training on social engineering tactics, safe internet browsing, and proper device security measures. Establish clear policies for personal device usage, data sharing, and communication protocols. Regular security awareness testing through simulated phishing exercises helps identify training needs and reinforce learning. Document training completion, provide ongoing resources for security questions, and maintain current training materials reflecting evolving threat landscapes and security requirements.
Question: How should businesses monitor and audit cloud accounting system security?
Answer: Monitor cloud accounting security through automated logging of user activities, regular access reviews, and continuous monitoring for unusual account behaviors or unauthorized access attempts. Implement security information and event management (SIEM) systems where appropriate, conduct regular security assessments, and maintain audit trails for all financial transactions and system changes. Use dashboards for real-time security monitoring, establish alert systems for suspicious activities, and conduct periodic penetration testing or vulnerability assessments. Regular compliance audits ensure adherence to security policies and regulatory requirements. Document all monitoring activities, investigate security incidents promptly, and maintain updated incident response procedures for various threat scenarios.
Question: What compliance considerations apply to cloud accounting security for remote teams?
Answer: Compliance considerations for cloud accounting security include data protection regulations (GDPR, CCPA), industry-specific requirements (SOX, HIPAA), and professional standards for accounting firms. Ensure cloud providers meet relevant compliance certifications (SOC 2, ISO 27001), maintain data residency requirements for international operations, and implement audit trails required by regulatory standards. Document security procedures, conduct regular compliance assessments, and maintain evidence of security control effectiveness. Consider privacy impact assessments for personal data processing and ensure contracts with cloud providers include appropriate compliance provisions. Professional consultation helps navigate complex compliance requirements and ensure adequate security measures meet applicable standards.
Question: How can businesses evaluate and select secure cloud accounting platforms for remote teams?
Answer: Evaluate cloud accounting platforms by assessing security certifications (SOC 2, ISO 27001), data encryption standards, access control capabilities, and audit trail functionality. Review provider security policies, data center locations, backup procedures, and incident response capabilities. Evaluate integration security with existing systems, user authentication options, and administrative controls available. Consider provider financial stability, customer support quality, and compliance with relevant regulations. Request security questionnaires, review third-party security assessments, and consider trial periods to evaluate security features. Professional security assessments may help evaluate complex requirements and ensure chosen platforms meet organizational security standards and compliance needs.
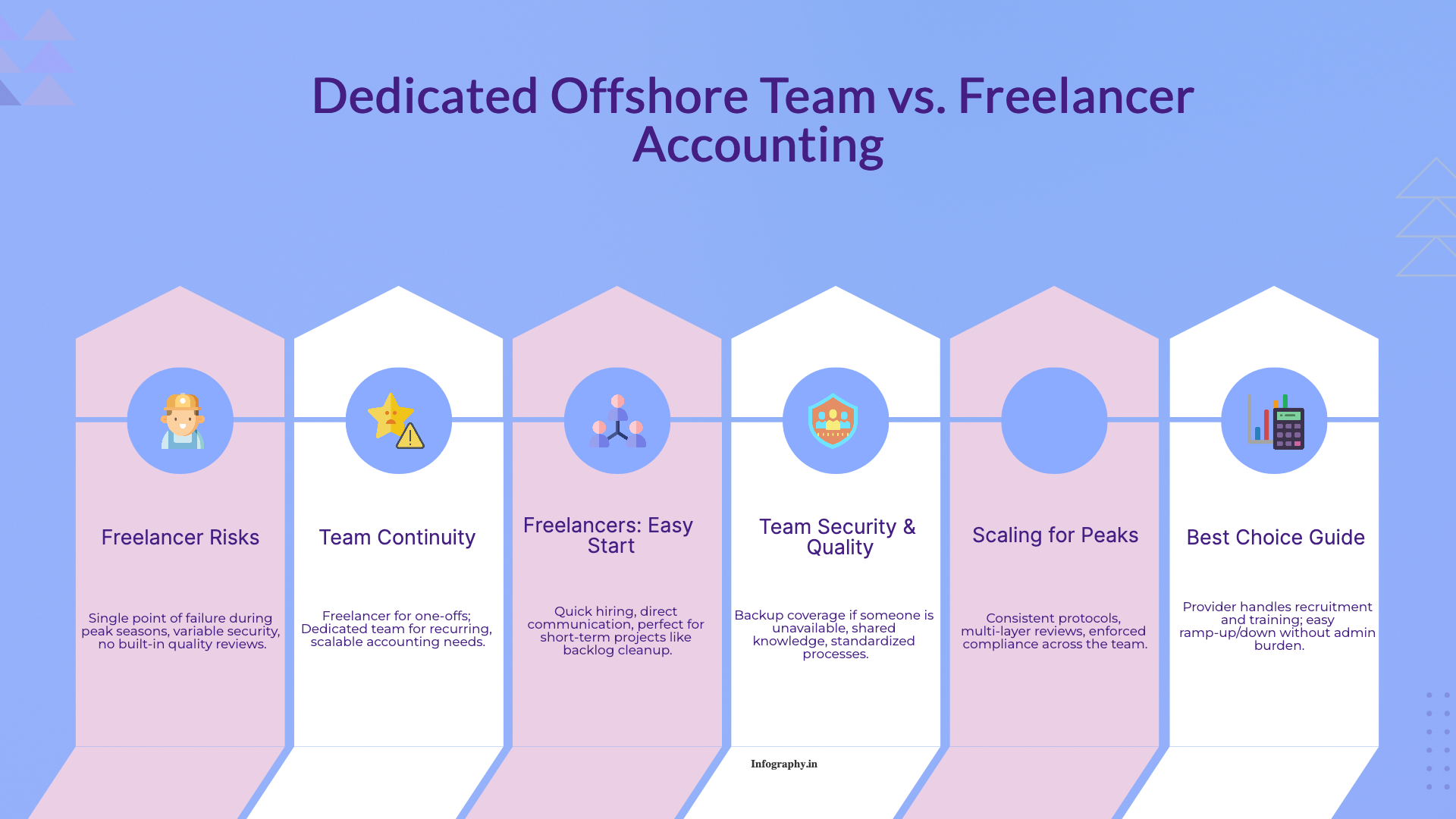
A practical comparison of hiring a freelancer vs using a dedicated offshore accounting team, focusing on continuity, quality control, security, and scaling.
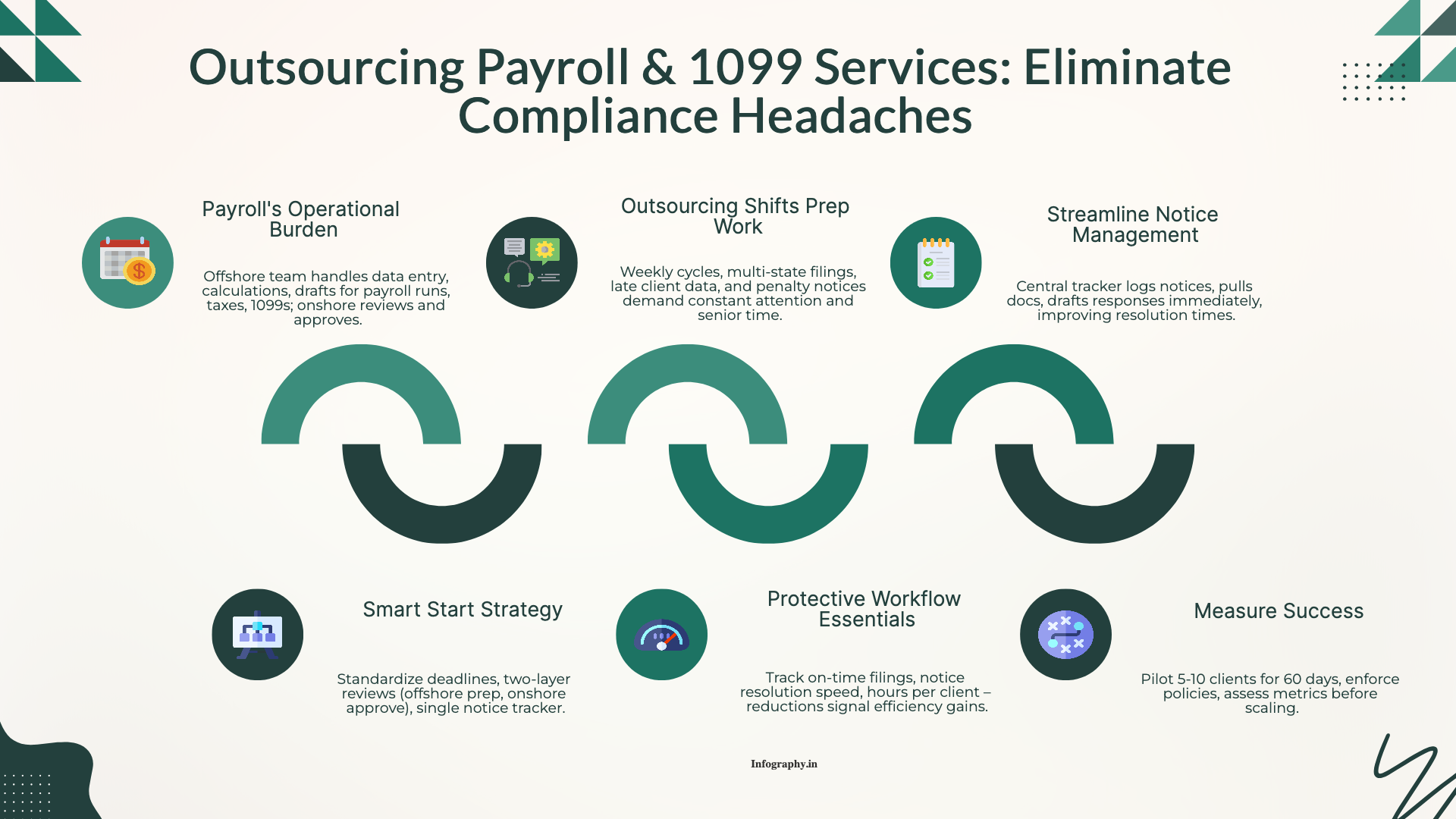
How CPA firms outsource payroll and 1099 work to reduce penalties and admin load, with a clean workflow for approvals, filings, and year-end reporting.

Practical do's and don'ts for CPA firms outsourcing accounting work, based on common failure points and what successful rollouts do differently.