Fraud statistics show that 60% of small businesses experience fraud, with an average loss of $200,000 per incident. 85% of fraud is committed by employees, and 70% of fraud cases last over a year before detection.
Small businesses are vulnerable because they have limited resources for security, trust in employees, lack of internal controls, and inadequate oversight.
Asset misappropriation includes theft of cash or inventory, false expense reimbursements, payroll fraud, and check tampering. Financial statement fraud involves revenue manipulation, expense misclassification, asset overvaluation, and liability understatement. Corruption includes bribery and kickbacks, conflicts of interest, bid rigging, and vendor collusion.
Pressure or motivation comes from financial problems, personal debt, lifestyle maintenance, and addiction issues. Opportunity or access comes from weak internal controls, lack of oversight, trust in employees, and inadequate systems. Rationalization or justification includes thoughts like "I'll pay it back," "I deserve more," "The company can afford it," and "Everyone does it."
To reduce pressure, offer employee assistance programs, fair compensation, open communication, and financial education. To eliminate opportunity, implement strong internal controls, regular oversight, segregation of duties, and monitoring systems. To address rationalization, create clear policies, ethics training, positive culture, and consequences for violations.
This means no single person controls the entire process. Different people handle different functions with cross-checking and verification. You need independent oversight. Key separations include receipt and recording, authorization and execution, custody and record-keeping, and reconciliation and review.
For expense approval, require pre-approval for large expenses, multiple approval levels, documentation requirements, and regular review. For payment authorization, use dual signatures for checks, electronic payment controls, vendor verification, and regular reconciliation.
For cash handling, limit cash on hand, use secure storage, conduct regular counts, and require witness requirements. For inventory management, use secure storage, access controls, regular counts, and documentation.
For user access, implement role-based permissions, regular access reviews, strong passwords, and multi-factor authentication. For system controls, use audit trails, transaction limits, approval workflows, and regular backups.
For banking security, use dual signatures, online banking limits, regular reconciliation, and fraud monitoring. For payment controls, set ACH limits, wire transfer controls, vendor verification, and regular review.
Conduct background checks including criminal history, credit reports, reference checks, and employment verification. Use an interview process with behavioral questions, scenario testing, reference interviews, and multiple interviews.
Conduct performance reviews with regular evaluations, goal setting, feedback sessions, and development plans. Provide training and education on fraud awareness, ethics training, policy updates, and security procedures.
Daily tasks include reviewing bank statements, checking cash receipts, monitoring expenses, and verifying transactions. Weekly tasks include reconciling accounts, reviewing reports, checking approvals, and monitoring trends. Monthly tasks include financial analysis, variance review, budget comparison, and trend analysis.
Behavioral red flags include living beyond means, financial problems, unusual behavior, and reluctance to take vacation. Financial red flags include unexplained transactions, missing documentation, inconsistent records, and unusual patterns.
Take immediate actions by securing evidence, notifying authorities, preserving records, and limiting access. Follow an investigation process by documenting everything, interviewing witnesses, gathering evidence, and calculating losses. Focus on recovery efforts through insurance claims, legal action, asset recovery, and system improvements.
Improve systems by strengthening controls, improving monitoring, enhancing security, and conducting regular audits. Change culture through ethics training, open communication, whistleblower programs, and positive reinforcement.
Types of coverage include employee dishonesty, computer fraud, funds transfer fraud, and social engineering. Consider coverage limits, deductibles, exclusions, and claims process.
Documentation includes clear policies, employee agreements, confidentiality agreements, and non-compete clauses. Ensure compliance with labor laws, privacy regulations, industry standards, and best practices.
Set the tone at the top with ethical leadership, clear expectations, consistent enforcement, and open communication. Develop policies with written policies, regular updates, employee training, and clear consequences.
Provide training programs on fraud awareness, ethics education, policy training, and security procedures. Maintain communication through regular updates, open dialogue, feedback channels, and recognition programs.
Accounting software should have built-in controls, audit trails, exception reporting, and user monitoring. Specialized tools include fraud detection systems, analytics software, monitoring tools, and alert systems.
Protection measures include encryption, access controls, regular backups, and security updates. Monitoring includes system logs, access reports, exception alerts, and regular reviews.
Fraud prevention isn't just about catching bad actors. It's about creating a culture of integrity and implementing systems that make fraud difficult to commit and easy to detect. The cost of prevention is always less than the cost of fraud.
Start with the basics: segregate duties, implement controls, and monitor regularly. Then build a culture of ethics and transparency that makes fraud not just difficult, but unthinkable.
Ready to strengthen your fraud prevention? Check out our comprehensive guide on In-House vs. Outsourced Accounting: A Cost-Benefit Analysis to understand your options.
For insights on working with external teams, read our article on Best Practices for Working with an Offshore Accounting Team.
And if you're ready to take the next step, our guide on How to Choose an Accounting Outsourcing Provider: 10 Questions to Ask will help you select the right partner.
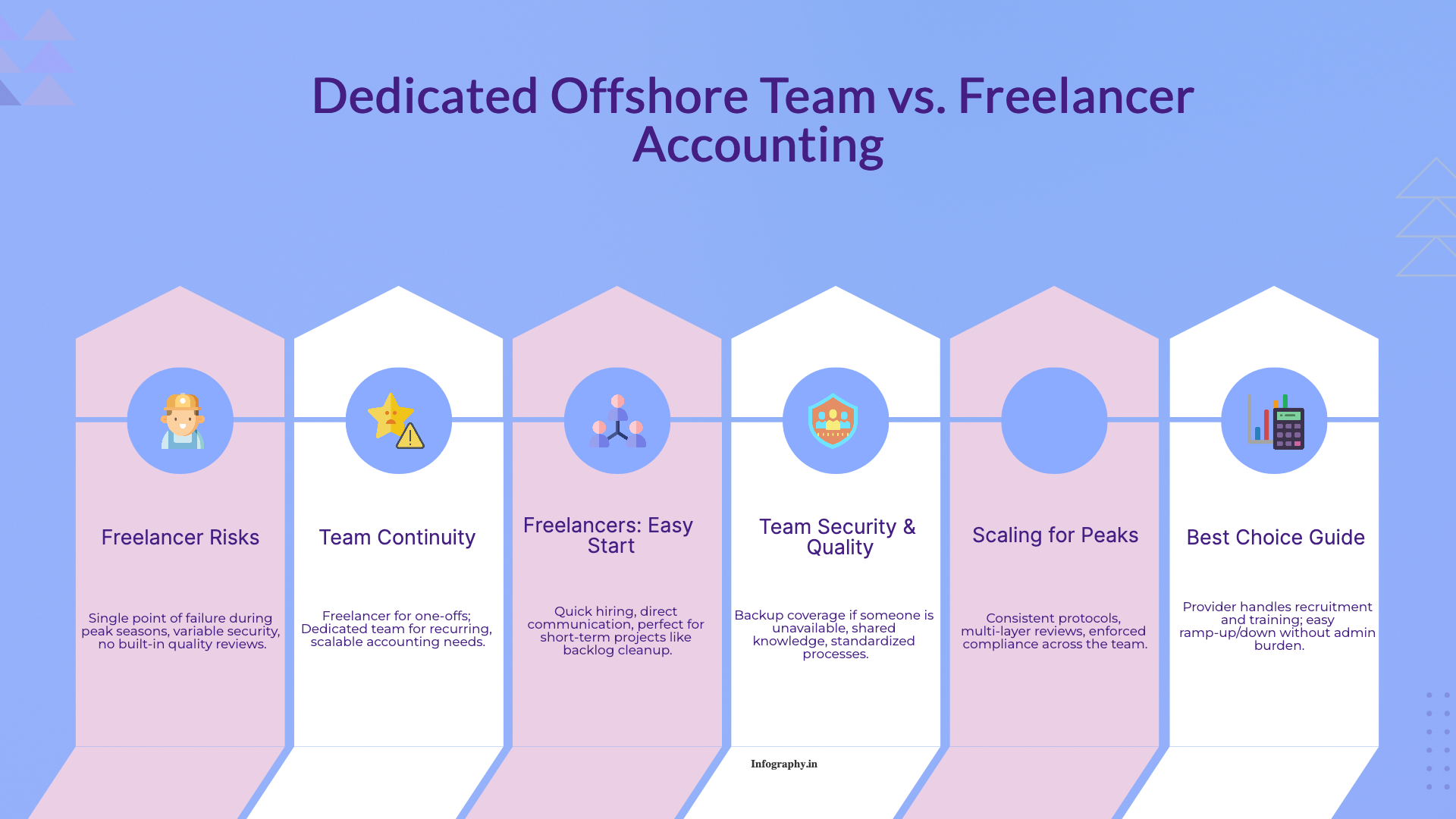
A practical comparison of hiring a freelancer vs using a dedicated offshore accounting team, focusing on continuity, quality control, security, and scaling.
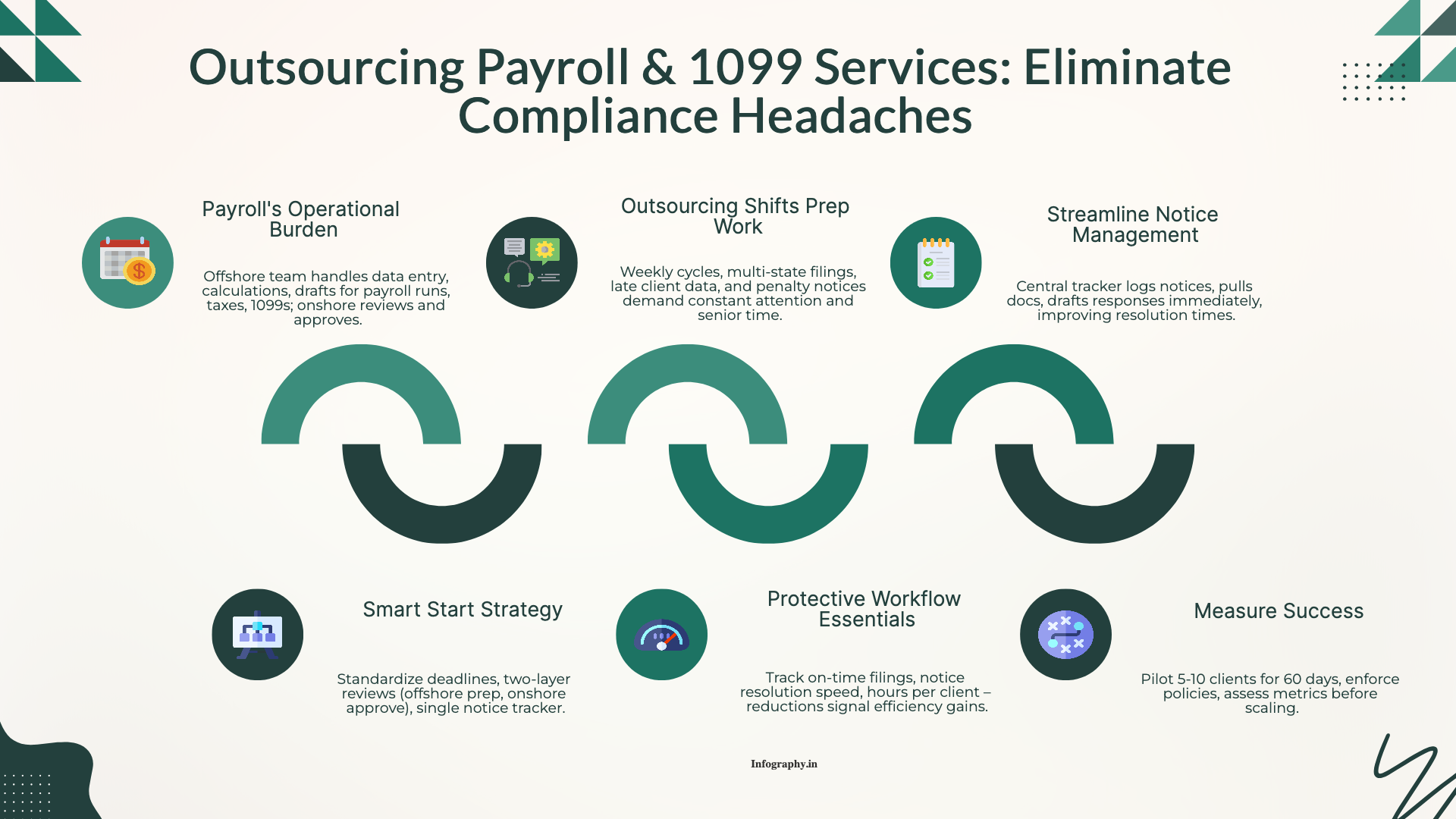
How CPA firms outsource payroll and 1099 work to reduce penalties and admin load, with a clean workflow for approvals, filings, and year-end reporting.

Practical do's and don'ts for CPA firms outsourcing accounting work, based on common failure points and what successful rollouts do differently.