Outsourcing helps firms scale work without adding fixed cost. It can also add risk if vendor controls are not clear. Vendor due diligence is a simple process that checks security, privacy, and reliability before you send client data. The goal is to show that a partner can protect records, keep systems available, and respond if something goes wrong. You do not need a heavy process to get this right. You need a clear scope, the right documents, and steady follow up.
SOC 2 reports describe how a service organization protects systems and data. They cover trust service criteria like security, availability, processing integrity, confidentiality, and privacy. Type 1 looks at design at a point in time. Type 2 looks at design and operating effectiveness over a period.
ISO 27001 is a standard for an information security management system. It focuses on risks, policies, controls, and ongoing checks. A vendor can show a current certificate and a statement of scope. Together, these frameworks give you a strong base for accounting vendor security due diligence. You still need to read what is in scope and how it matches the work you plan to send.
Before you ask for reports, write what you plan to outsource. List the processes, systems, and kinds of data that will move. Client ledgers, payroll records, tax files, and bank details each carry different risks. Draw a simple data map that shows where information comes from, where it is processed, and where it is stored. This helps you test if the vendor’s SOC 2 or ISO 27001 scope covers your real flow. It also keeps the review focused.
Start with a short call. Confirm location, entity name, years in business, and the work they do for firms like yours. Ask if they hold a current SOC 2 Type 2 report, an ISO 27001 certificate, or both. Ask about the last independent audit date. Confirm that controls cover the sites and platforms used for your services. Note any subcontractors or cloud providers that are in the path.
If a vendor has no current report or certificate, ask when one will be ready. If there is no plan, consider a safer option or reduce scope. A pre-screen saves time for both sides.
Request only what you will read. A focused list works best. Ask for the SOC 2 Type 2 report for the last period. Ask for the ISO 27001 certificate and the statement of applicability. Ask for a summary of penetration tests, a recent vulnerability scan summary, and an overview of policies. If work includes personal data, ask for a privacy policy and data processing terms. If the vendor uses subcontractors, ask for a current list and the controls they flow down.
When you receive these, check dates, scope, and exceptions. If the SOC 2 period ended long ago, request a bridge letter that explains changes since the end date. If the ISO scope excludes the platform used for your work, note the gap and ask how they plan to cover it.
Check how users are added, changed, and removed. A vendor should have role based access, approval before access, and prompt removal when staff leave. Multi factor login should be in place for admin access and remote work. For client tools, confirm that least privilege is used and that login is unique to each person.
Confirm that data is encrypted in transit and at rest. Ask which protocols are used for network traffic. Ask who manages keys and where they are stored. If the vendor handles backups, confirm that backups are encrypted and tested.
Ask how the vendor controls changes to systems that will touch your data. A simple process should cover request, approval, testing, and rollback. Confirm that developers do not have direct access to production data unless there is a clear break glass rule with logging.
Check that the vendor logs activity that matters. Admin actions, failed logins, and access to client records should be logged. Ask who monitors the logs and how often. Confirm that alerts route to a team that can act.
Ask for an incident response summary. It should name roles, steps, and time frames. Confirm how and when you will be notified if an event affects your data. Ask if the vendor has tested the plan in the last year.
Outsourced accounting relies on steady access. Confirm that the vendor has a plan for loss of a site, a network, or a key system. Ask for recovery time and recovery point goals. Ask when the plan was last tested and what changed after the test.
Check how long the vendor keeps data and where. Confirm that they can delete client records on request. If they use backups with long retention, ask how they handle legal holds and deletion requests that arrive after a backup is made.
If the work includes personal data, check lawful bases, consent, and rights requests. Confirm if the data stays in one region or moves across borders. If data will move, ask how the vendor handles transfer rules.
Most vendors rely on cloud platforms and point tools. Ask for a list. Confirm that core providers hold strong certifications and that the vendor reviews them each year. If a subcontractor handles any part of your process, confirm that the same controls apply.
After you review, write a short risk score. Use a simple scale like low, medium, or high for each area. Note factors that raise risk, such as old reports, large exceptions, or missing logs. Note factors that reduce risk, such as a recent SOC 2 Type 2, broad ISO scope, and strong offboarding. Decide if you will proceed, proceed with limits, or stop. If you proceed with limits, write what data and processes are in scope and what must wait until gaps close.
Put security terms in the contract. Include confidentiality, data protection, breach notice, and audit rights. Add access rules, change control, and record retention. For client data, include deletion at end of term. If the vendor will use subcontractors, require notice and your approval.
During onboarding, start small. Give access to test data first. Train both teams on how to use your systems, how to move files, and how to report issues. Confirm that vendor users are named, unique, and tied to a role. Set up a shared tracker for tasks, issues, and fixes.
Due diligence is not a one time task. Set a simple annual cycle. Ask for new SOC 2 reports and ISO certificates when they renew. Review exceptions and management responses. Hold a short quarterly check to review changes to staff, systems, and subprocessors. Test access lists each quarter. Remove users who no longer need access. If work volume grows, raise the level of review.
Keep a short scorecard that shows the vendor’s status at a glance. Include report dates, incident counts, and time to resolve issues. Share the scorecard with leaders so they see the trend.
Offshore capacity can add time zone coverage and lower cost. It also adds items to watch. Confirm where staff are located and which laws apply to data. Use multi factor login and device rules for remote access. Keep work in your systems when possible. If files must move, use an approved secure tool and track transfers. Set a clear rule for client contact. In most cases, the vendor should not contact your clients unless you approve it. Build a short training that covers your firm’s privacy policies and client standards.
Week 1 is for scope and pre-screen. Write the process in scope and make the data map. Hold the first call and request documents. Week 2 is for review. Read the SOC 2 report, the ISO material, and the policy summaries. List gaps and questions. Week 3 is for answers and scoring. Meet to close questions, write the risk score, and decide. Week 4 is for contract terms and a small pilot. Set roles, grant access, and run a limited test with non production data. Move to live work after the pilot meets your checks.
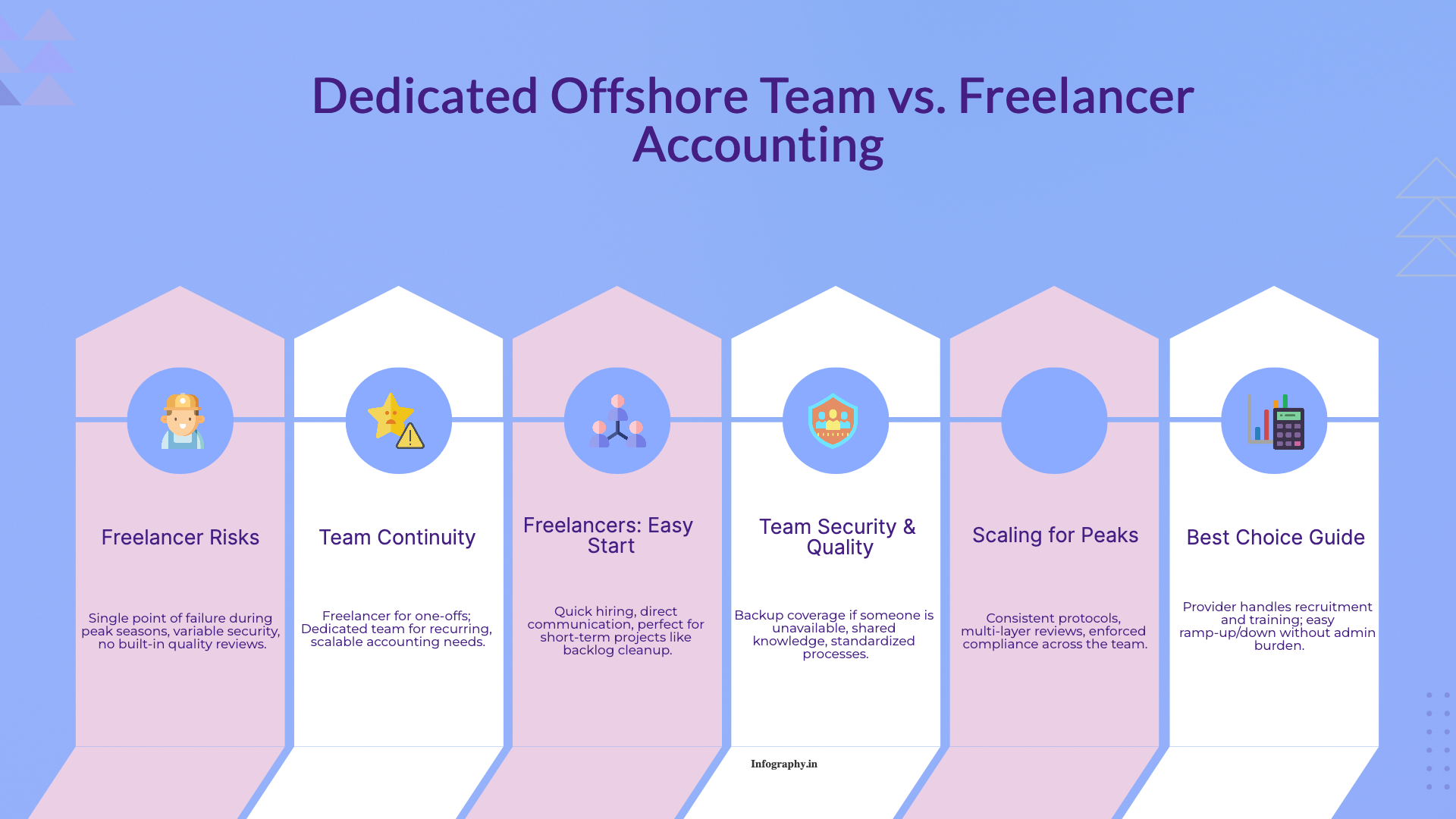
A practical comparison of hiring a freelancer vs using a dedicated offshore accounting team, focusing on continuity, quality control, security, and scaling.
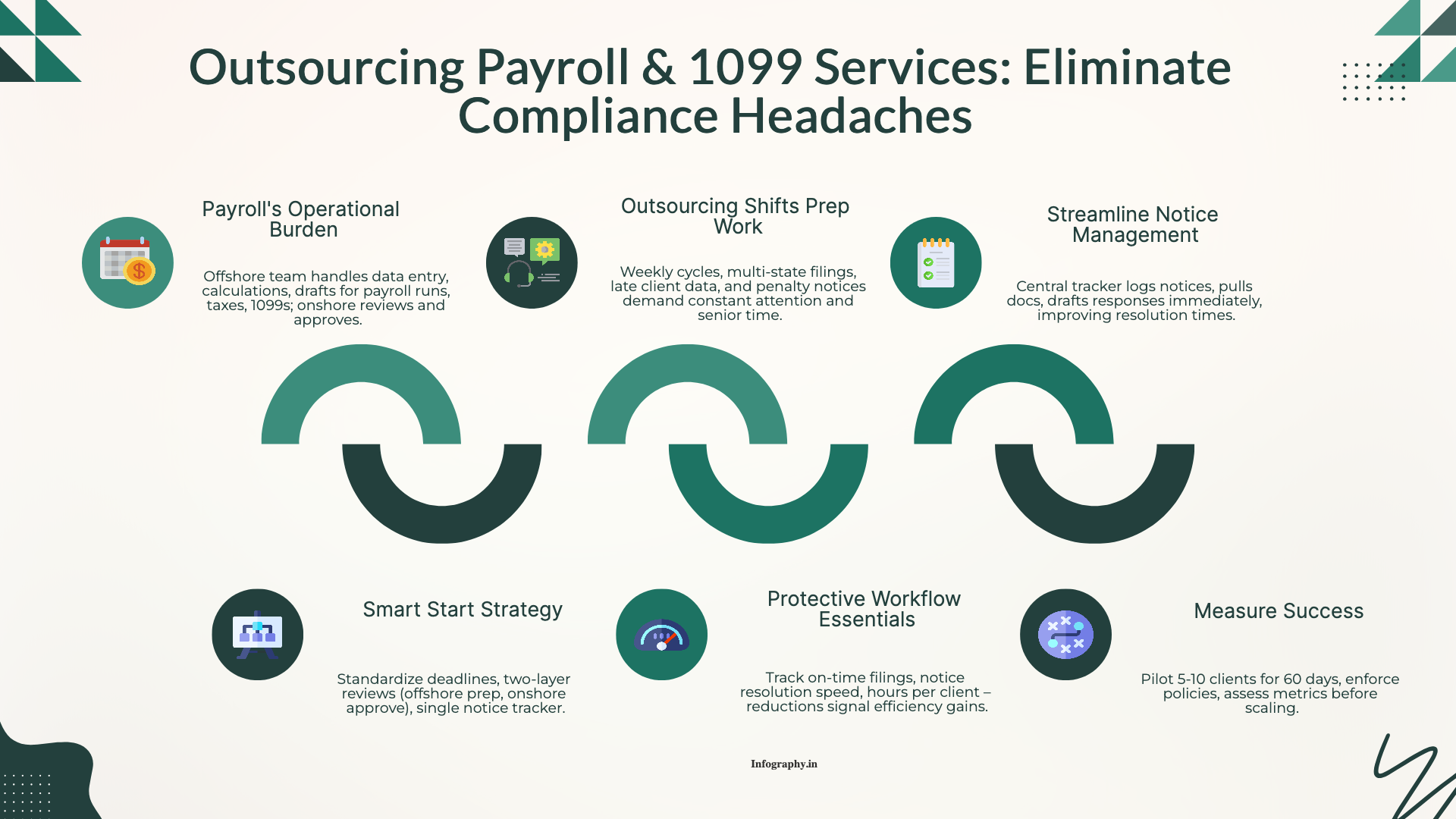
How CPA firms outsource payroll and 1099 work to reduce penalties and admin load, with a clean workflow for approvals, filings, and year-end reporting.

Practical do's and don'ts for CPA firms outsourcing accounting work, based on common failure points and what successful rollouts do differently.