Choosing an offshore accounting partner should feel safe, not risky. Yet the moment you share payroll, customer, or financial data with a third party, you inherit their security posture. This buyer’s guide breaks down what certifications actually mean, what your DPA must cover, how to evaluate sub-processors, and how breach response should work in practice.
Before you ask for any certificate, map your own footprint:
This tells you what assurance you need: application-only, infrastructure, or both.
What it is. An attestation over controls relevant to security, availability, confidentiality, processing integrity, and privacy.
Type I vs Type II.
How to read it.
What to request. Latest SOC 2 Type II report, bridge letter, and any independent pen test summary relevant to in-scope systems.
What it is. Certification of a vendor’s Information Security Management System (ISMS) by an accredited body.
What to verify.
What to request. Current certificate, SoA, and a summary of recent surveillance audit findings and closures.
Roles. Identify controller vs processor for each data flow.
Core DPA terms to require.
What to request. Executed DPA, SCCs/IDTA with annexes, TIA, Record of Processing Activities (RoPA), and the vendor’s retention/deletion policy.
Ask for a current sub-processor list with services, locations, and DPAs. Ensure contracts flow down your security and privacy requirements. Require advance notice and an objection mechanism for material changes.
Minimum baselines for offshore accounting delivery:
Request policies and last completed reviews as evidence.
Expect:
Ask for scan summaries, patch metrics, and a pen test attestation.
A vendor should have:
Request the IR plan and last tabletop report. Confirm how you will be notified and how evidence is preserved.
Review RTO/RPO targets, last BCP/DR tests, and data-center/region failover plans. Ensure backups follow the same security controls and meet your retention rules.
Security due diligence should be practical. If a vendor can show current SOC 2 Type II or ISO 27001 with a clear scope, deliver a complete DPA with transfer documents, name their sub-processors, and walk you through incident and continuity drills, you have a strong baseline. Use the questionnaire to keep every claim tied to evidence.
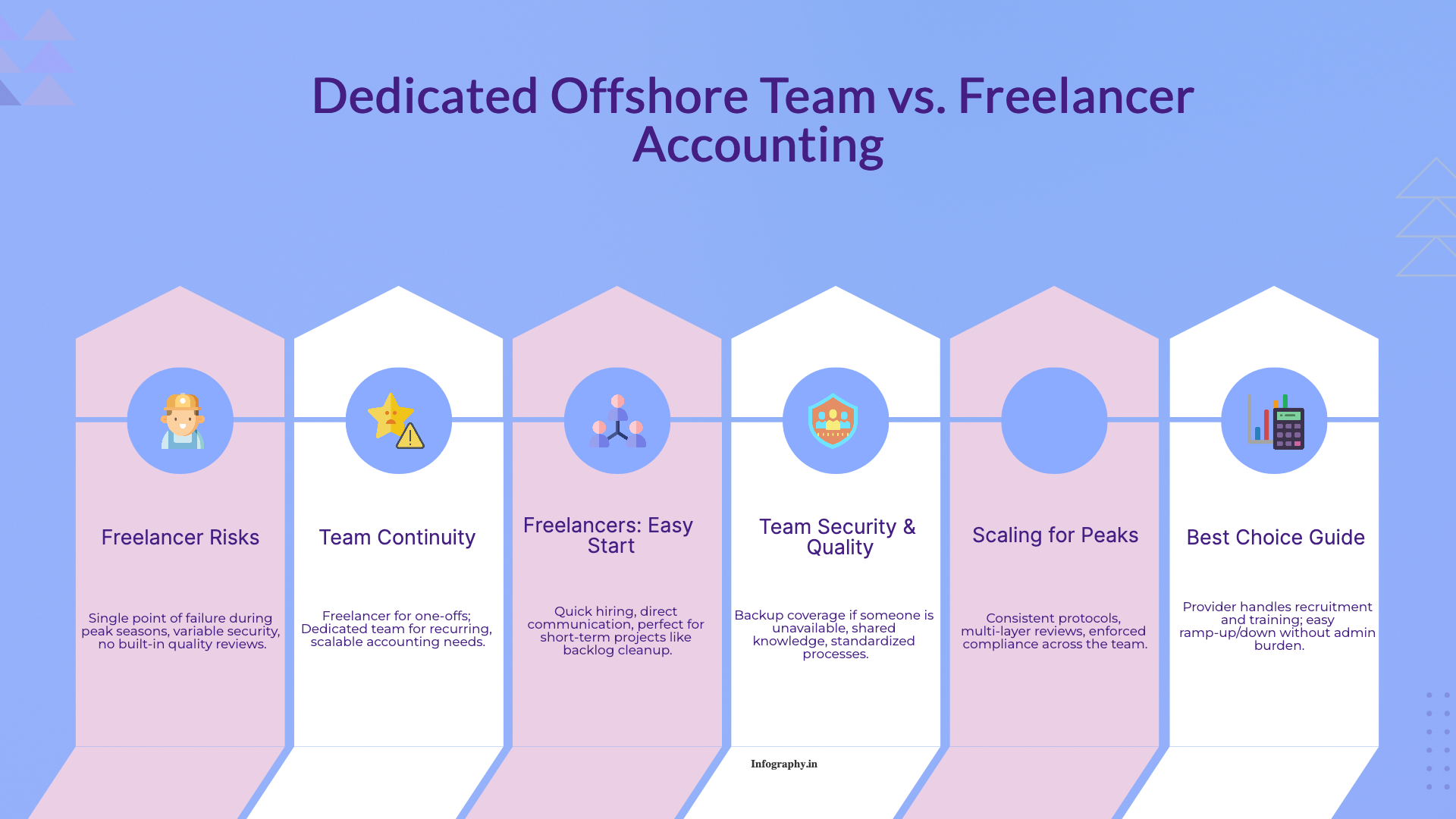
A practical comparison of hiring a freelancer vs using a dedicated offshore accounting team, focusing on continuity, quality control, security, and scaling.
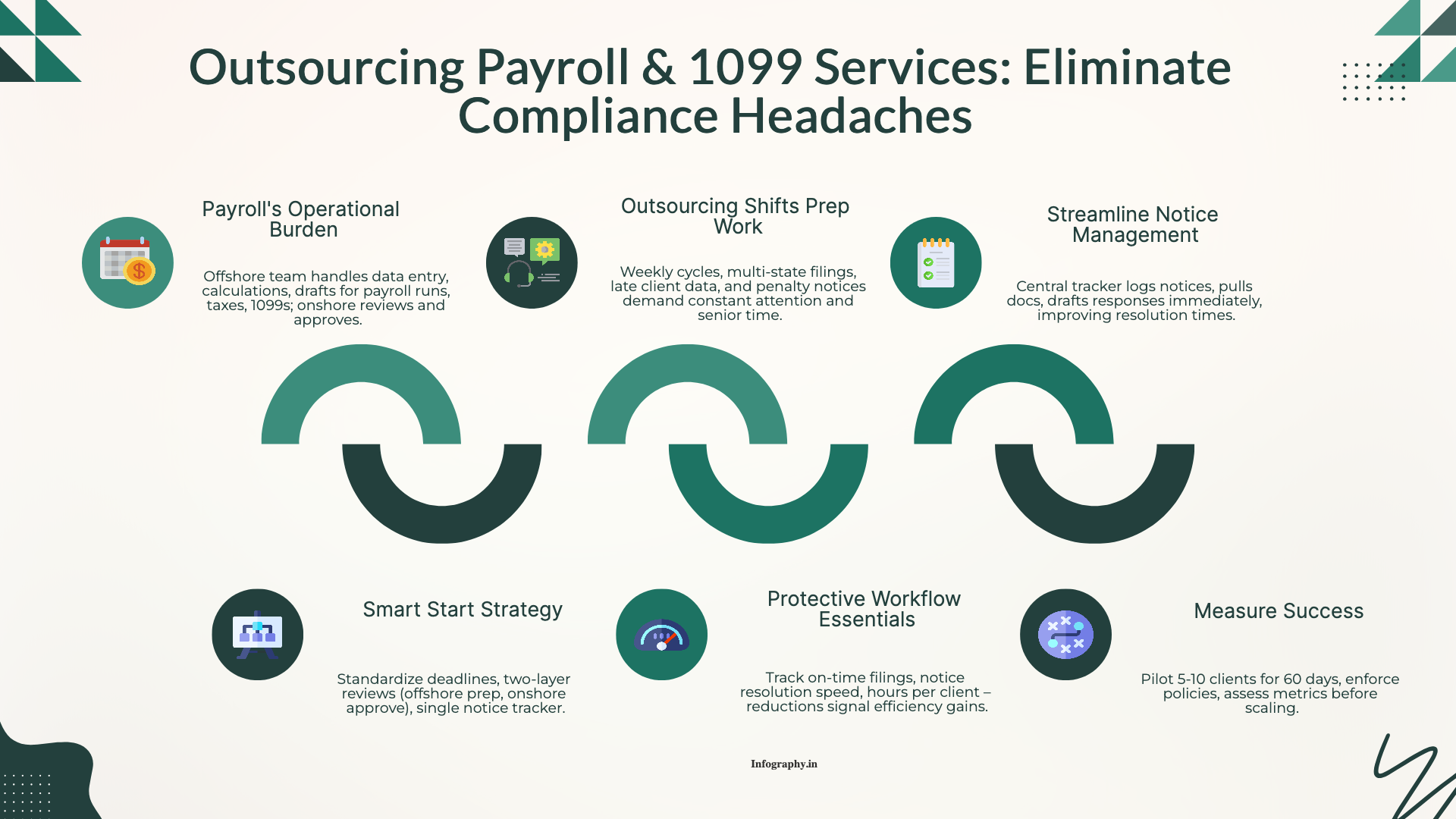
How CPA firms outsource payroll and 1099 work to reduce penalties and admin load, with a clean workflow for approvals, filings, and year-end reporting.

Practical do's and don'ts for CPA firms outsourcing accounting work, based on common failure points and what successful rollouts do differently.